Breaking the Chain- Exploiting Token Abuse for Lateral Movement
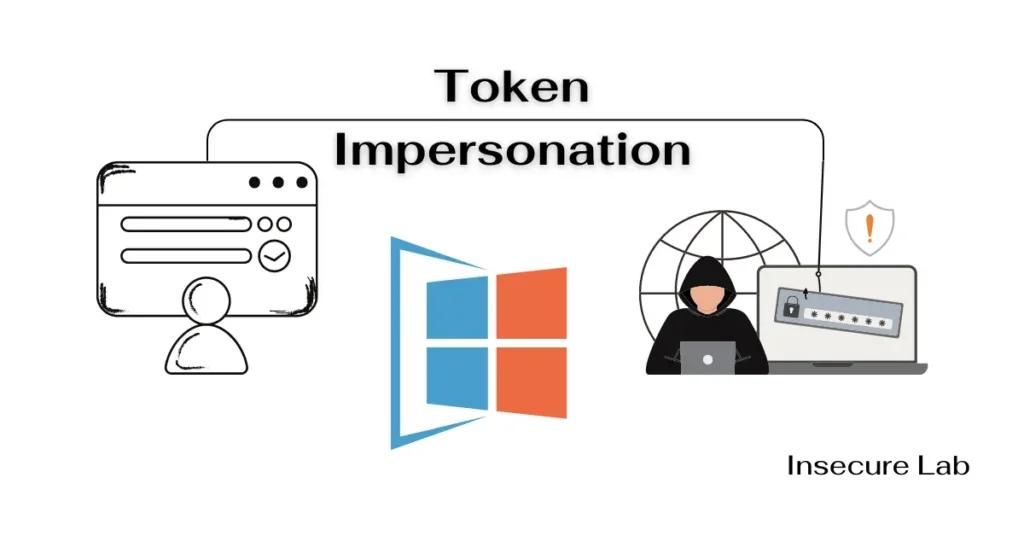
Penetration testers can steal a user’s identity without even breaking their password. This is done by simulating a token impersonation attack, which is more like a digital mask. A token is like a backstage pass users get when they log in to a system or software. In technical terms, a token is a data element […]
The Quantum Era is Approaching, And So Are Its Potential Risks

The advent of quantum computing is poised to revolutionize various industries, but it also presents significant cybersecurity challenges. Quantum computers have the potential to break current encryption methods, exposing sensitive government, military, and financial data to unprecedented risks. The superior computational capabilities of quantum computing can also make some encryption ciphers obsolete and hackable, defying […]
What Is DKIM— Definition, Procedure, And Challenges
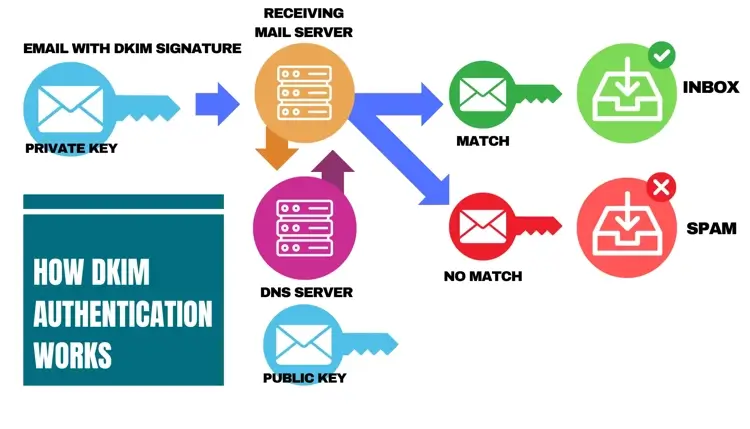
DKIM is short for DomainKeys Identified Mail. It is an email authentication protocol that a domain owner implements so that the receiving mail server can verify whether someone has altered the message content in transit. DKIM is very sensitive to alterations, so even an extra space or character can cause authentication to fail. Implementing DKIM […]
What Is SPF in Email Authentication— All About Its Working, Syntaxes, and Failure Mechanisms
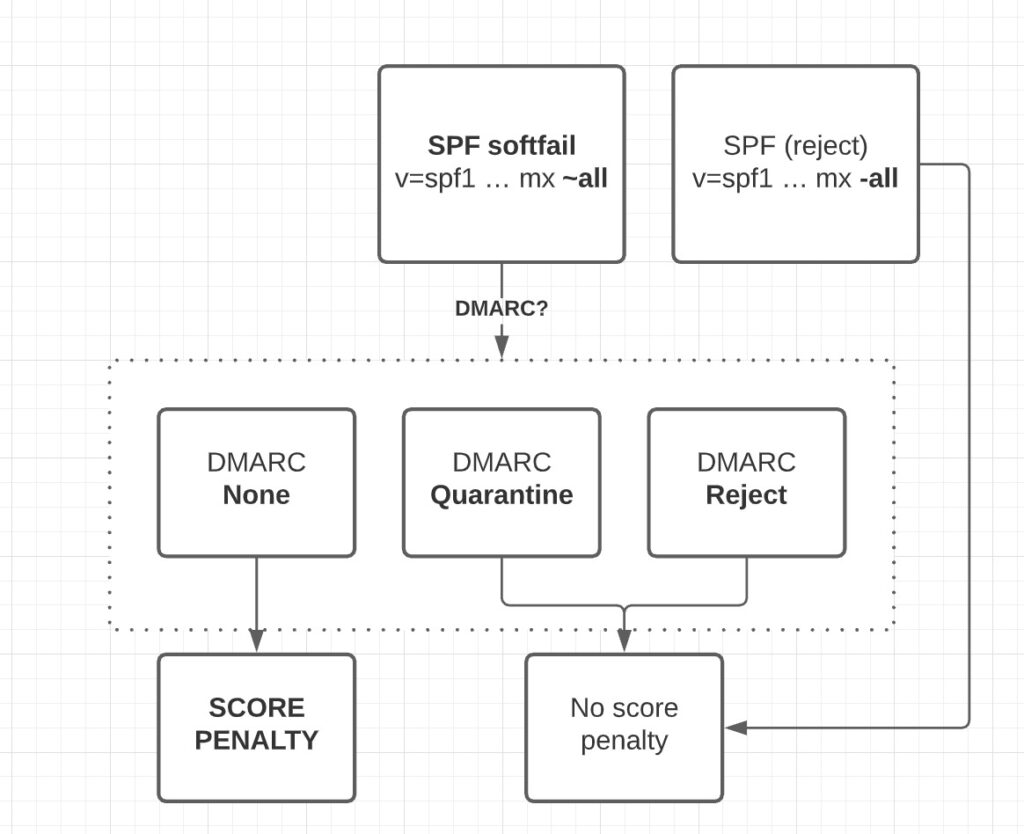
It’s 2025, and email-based cyberattacks continue to pose as significant financial, reputational, and operational threats to organizations. As per IBM’s recent report, the global average cost of a data breach in 2024 is $4.88 million— a 10% increase over the last year and the highest total ever. With such numbers surfacing the internet daily, it’s […]
The 5 Stages of Penetration Testing

Penetration testing (pen test for short) is an ethical hacking technique in which an attack is officially simulated against a company’s technical infrastructure to know about all the security loopholes a threat actor can exploit. In simpler words, a white-hat hacker tries breaking into different domains of a company’s technical system to come across all […]

