 SPF (Sender Policy Framework) is the foundation of your email authentication journey, and if you don’t get it right, you might run the risk of putting your entire domain at the mercy of attackers. That’s exactly what you were trying to avoid in the first place, right?
SPF (Sender Policy Framework) is the foundation of your email authentication journey, and if you don’t get it right, you might run the risk of putting your entire domain at the mercy of attackers. That’s exactly what you were trying to avoid in the first place, right?
When it comes to configuring SPF for your domain, the most important step that can make or break your setup is the SPF record— the part you publish in your DNS to define who is allowed to send emails using your domain.
And this is where most people mess things up.
For instance, they add +all at the end of the record, thinking it might help with email delivery. In reality, it does the opposite. It tells receiving mail servers to accept email from any IP address as if it were legitimate.
In this article, we will understand why you should never set your SPF record to +all.
The perils of the +all mechanism
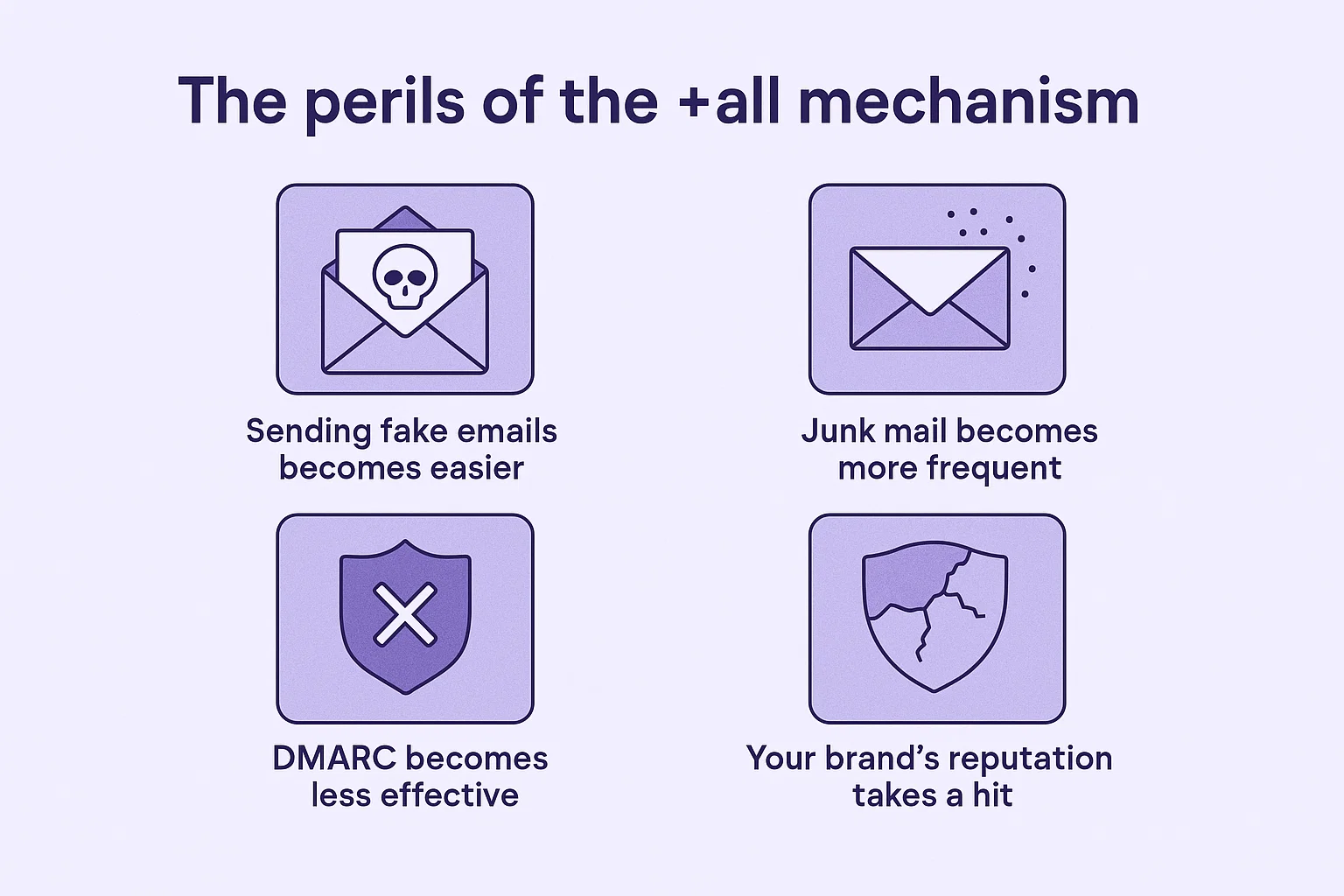
The +all mechanism tells the receiving server to approve messages from any IP address, even if they have nothing to do with you or your company.
You might think that you’re improving delivery by taking a lenient stance, but essentially, you are inviting cyberattackers to impersonate you and dupe your clients.
Here’s what can go wrong when you have the +all mechanism in place
Sending fake emails becomes easier
When you use +all, anyone can send emails that appear to be from you. These emails could attempt to trick people into providing passwords, banking information, or clicking on malicious links. Because the email appears to be sent from your domain, people are more likely to think it’s authentic. If something goes wrong, they’ll blame you for not protecting your domain.
Junk mail becomes more frequent
If you’ve used +all, spammers will see your domain as an easy target. They’ll send thousands of spam emails using your name, and soon, email services like Gmail and Outlook will stop trusting your domain. Even your genuine emails might start landing in the spam folder.
DMARC becomes less effective
Even if you’ve set up DMARC, +all can mess it up. DMARC relies on SPF or DKIM to fail in order to block a fake email. But if SPF always passes because of +all, then DMARC might not work as expected, especially if DKIM isn’t set up properly. That means fake emails could still land in inboxes.
Your brand’s reputation takes a hit
If your domain is used to execute a scam, your customers might lose confidence in your brand. And in sensitive industries such as banking or healthcare, it would also mean getting into legal trouble.
Struggling to get your point across to your clients and get them started with their email authentication journey?
Hi, I’m Daksh Kaur, and I am here to help you explain the ins and outs of email authentication and cybersecurity in a way your clients will actually understand — and act on. Reach out to me at daksh@turtlewords.com and let’s get started with building a blog section that educates, converts, and builds trust.

